Valimail Defend
Email Defender Soulation
800+
Happy Clients
1900+
Projects Completed
30+
Business Partners
6
Countries
DEFEND YOUR INBOX AGAINST PHISH
Keep your inbox safe from hacking emails
Card Readers
Accessible with industry-standard Wiegand and clock/information yield, are perfect with numerous OEM get to control frameworks. Peruse low vitality (charge card) or high vitality attractive stripe cards. The per-user interprets card data to choose Wiegand arranges as required by the OEM’s controller.
Valimail’s defender uses zero trust email security approach for absolute safety by quickly verifying each sender that sends your email and cross your secure email gateway in opposition to our data archive of more than 30 million Trustworthy .worthy domains. Furthermore, it instinctively contemporizes your concern contact list to our most trust-worthy shipper database. Once you are all done setting up the strategy, defend instinctively react on your all messages based on the procedure or plan and give shielding to all of your workers and by putting an end to all the incorrect positives. If the person who sends you mail is trusted, then the mail stays in worker inbox. But if the sender comes out to be not verified, the mail is indicated and moved to the group strategy. Cybersecurity solutions are that straight forward.
Key Characteristics

Guideline Control at Your Fingerprint
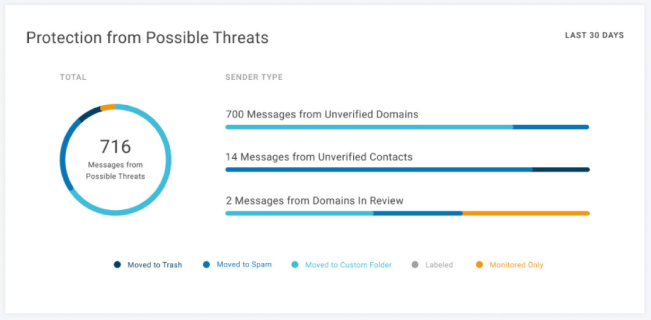
Protection provides entry to a large diversity of guideline control and arrangement on how to deal with unverified email traffic. The manager can allocate plans for the watch list, single mail slot, and traffic from the domain by following the steps.
- Transfer to spam
- Transfer to trash
- Transfer to custom file
- Attach label
- Scan only
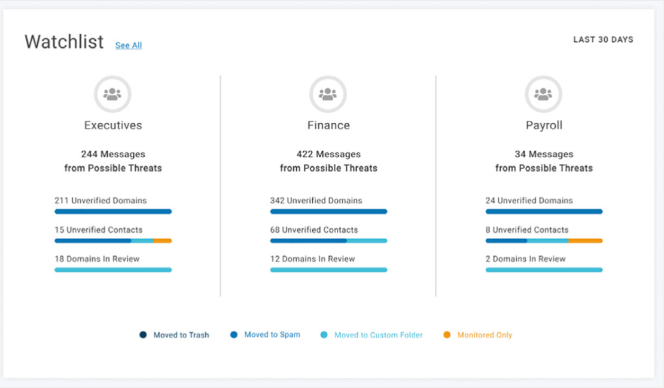
Shield Your Most Striked People
KEY BENEFITS
Stop Hacking Attacks
One-click Combination
No-trust, Identification-based inbox shielding
Straight Forward Strategy Arrangement
Grabs what existing solutions miss
Comprehensive Reporting
HOW IT WORKS
The World’s Largest Repository of Trusted Domains
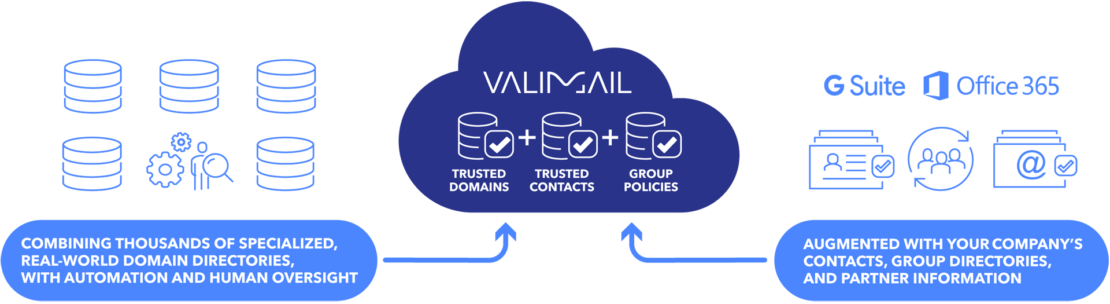
Valimail, the first of its kind, an evolving Identity-based, anti-fraudulent company that has been successful in ensuring the trustworthiness of its clients in terms of digital transmission of data around the globe since 2015. Valimail delivers a safe, cloud-native platform and authorizes the senders’ data and identity to check whether or not there is a harmful entity that may damage or
exploit you, your data, or your privacy in any way. Valimail ensures their clients or users to show submissiveness and agreement to its rules and regulations to protect your brand and help it grow stronger. Valimail offers its services and authenticates large sums of data for some of the biggest and eminent organizations of the world including Uber, Splunk, Yelp, Fannie Mae, Mercedes Benz USA, and the U.S, and has won more than a dozen reputable Cyber Security Technology awards which shows that the company has been more than successful so far.
For more information visit www.valimail.com.

Drop Us A Line
# Basrah, Algeria District, near Benghazwan Hospital.

The Power of Surveillance: Effective CCTV Solutions for Iraq

Navigating the Digital Landscape in Iraq: Top 5 IT Solutions

